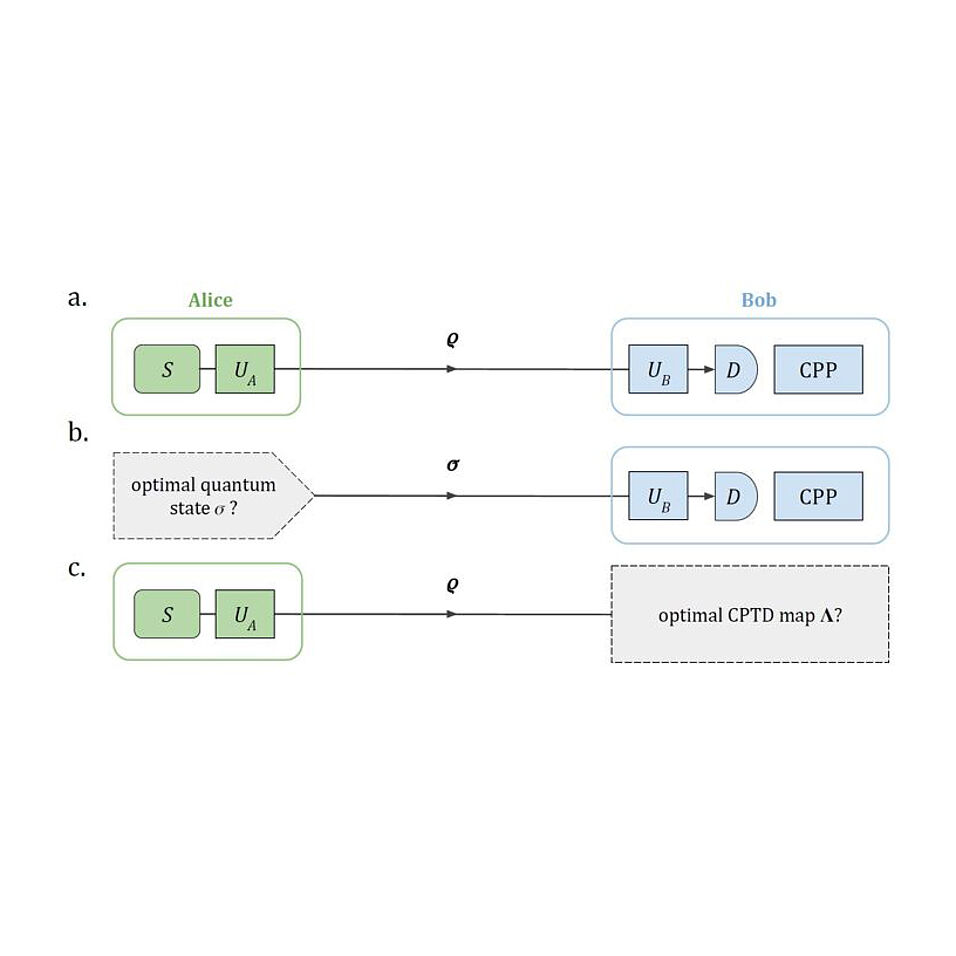
Abstract
Owing to its fundamental principles, quantum theory holds the promise to enhance the security of modern cryptography, from message encryption to anonymous communication, digital signatures, online banking, leader election, one-time passwords, and delegated computation. While quantum key distribution (QKD) has already enabled secure key exchange over hundreds of kilometers, a myriad of other quantum-cryptographic primitives are being developed to secure future applications against quantum adversaries. This review surveys the theoretical and experimental developments in quantum cryptography beyond QKD over the decades, along with advances in secure quantum computation. It provides an intuitive classification of the main quantum primitives and their security levels, summarizes their possibilities and limits, and discusses their implementation with current photonic technology.
- M. Bozzio, C. Crépeau, P. Wallden, P. Walther
Quantum cryptography beyond key distribution: Theory and experiment
Reviews of Modern Physics 97, 045006 (2025).